What is the “Dark Web”?
You probably have heard dark web scanning is a great way to prevent a data breach. But what does that even mean? The Dark Web is a part of the World Wide Web that uses darknets or overlays and is only accessible through specific software programs such as TOR browser. Unlike the surface web, the deep web is not indexed on search engines like Google and Bing. Using the Dark web, individuals on private networks can conduct business on dark web marketplaces and communicate anonymously without giving up identifying information such as location. A dark web marketplace serves as a digital black market allowing criminals to gain access of leaked data and personal information without the ability to be tracked down. Dark web sites conduct criminal activity through the sell and distribution of credit card details, medical records, passwords and other sensitive information. All being bought and sold relatively inexpensively. Worse, the information being sold, can be sold over and over again to many “dark agents” giving multiple potential hackers access to user accounts and other stolen data.
The loss of employee or company data can be devastating to an organization for multiple reasons. The costs of recovering it can be extraordinary, as well as the reputational losses if you legally or morally need to let your clients and vendors know you have experienced a breach.
This is why some organizations choose to run ongoing dark web scans for domains within their organization. Now, you might ask, “What exactly is dark web scanning?” Dark web scans are done by dark web scanners, which are tools designed to find data leaks across the entire dark web. Cyber professionals scan the dark web for full or partial amounts of sensitive information affiliated with your company’s domains and IP addresses. The types of items normally found are business usernames, personal passwords, business passwords as well as other business and personal information. By gathering information about what data is floating around the dark web your IT team or provider can easily make the needed changes both in security (changing user names or passwords for example) and company security policy (not allowing personal emails to be used for company business for example.)
Why is dark web scanning important?
Human error is one of the leading causes of data breaches, so it’s important to have layers of security in order to protect your company. A dark web scan can help you find and fix human errors before they become a problem. Additionally, cybercriminals are always looking for new ways to steal information, and not being covered on the dark web means they have the upper hand. Dark web scanners can not only monitor your company’s sensitive data but also fight against those who threaten your company’s existence!
Dark Web Scan Proactive Monitoring
Having a dark web monitoring service on a regular basis is a smart idea for the following reasons:
- With so much now dependent on a digital world, it is a very good idea to have your company domains proactively monitored and reported on. There are simply too many credentials out there and so even a small % of stolen data can cost a company immensely.
- By actively monitoring the dark web as it pertains to your domains and company, your IT team or provider, over time can significantly lower the amount and types of data that are getting leaked. This can be done through training of the end user as well as network settings that could restrict the types of end user activities that result in data dumps.
Comprehensive Reporting
In addition to running a dark web scan and learning about credentials on the dark web, getting a comprehensive dashboard report is a great feature of most dark web monitoring services. These reports show management data that is floating on the dark web, along with insights as to how data breaches occurred, allowing the IT team to react and set up additional security system policies and procedures based on real data. (see example report page below.)
-
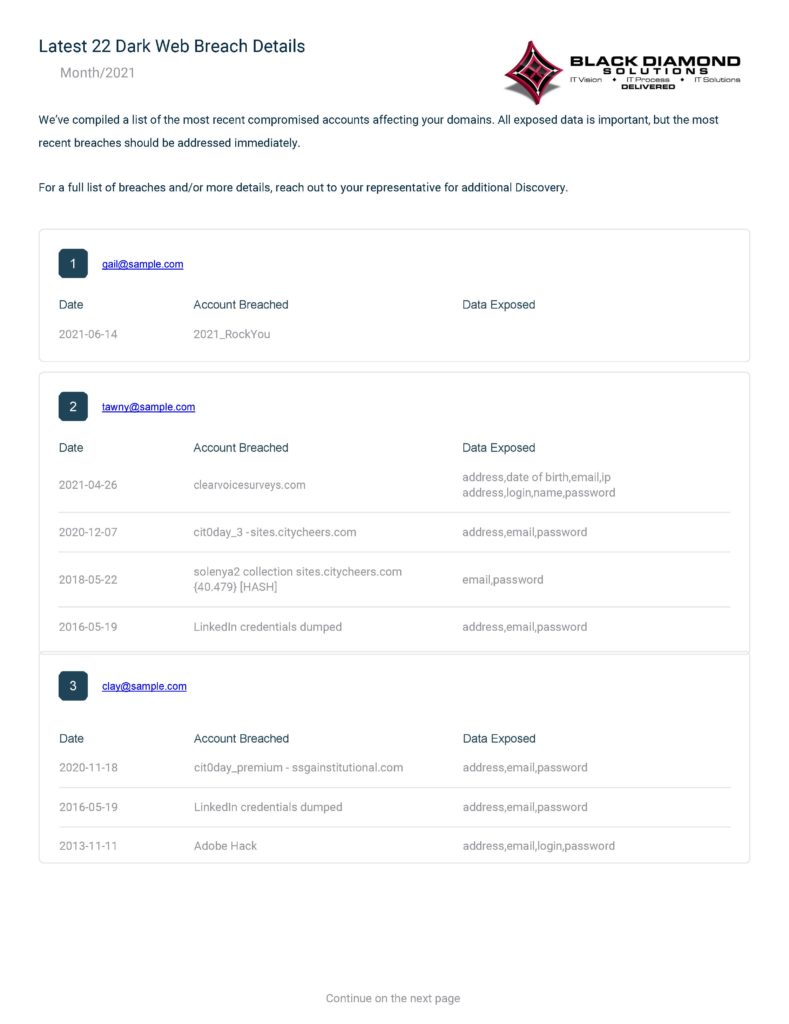
-
Sample Dark Web Scan Report
Dark Web Scans | Final Considerations
It is pretty clear to see the benefits of dark web scanning for any organization. It is easier to fight an enemy knowing you have the upper hand than hope you can gain that upper hand back after an account takeover occurs. A trusted team of cyber security professionals can help you gain that upper hand and keep it with proactive dark web monitoring. This special software helps fight against those that threaten your company’s existence. By gathering information about your personal data floating around the dark web, and analyzing comprehensive reports with insights, your IT team is better equipped to prevent a future data breach. If you’re concerned about this issue in your organization or want more information on dark web scanning, contact us today! We offer several security services designed to protect your personal information from leaking onto the dark web, so feel free to reach out with questions anytime!






