Can My Data Be Removed From the Dark Web? | Chicago Cybersecurity Experts Explain
At Black Diamond Solutions, we understand the growing concern over personal data security — especially in a time when cyber threats are accelerating. The dark web is a hidden layer of the internet used for illegal activities like selling stolen data, and once your personal information ends up there, it’s incredibly difficult to remove.
In this post, our Chicago-based cybersecurity team explains how the dark web works, why data removal is so difficult, and what proactive steps you can take to protect your identity and digital footprint. If you’re searching for dark web monitoring, data protection, or cybersecurity in Chicago, read on.
What Is the Dark Web and How Does It Work?
The dark web is a part of the internet not indexed by search engines like Google. It can only be accessed with special tools like Tor, which anonymize traffic by routing it through encrypted networks.
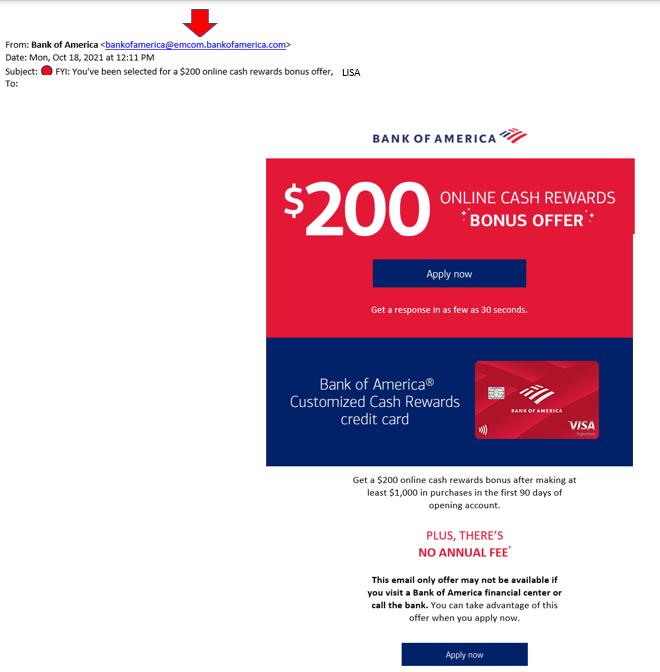
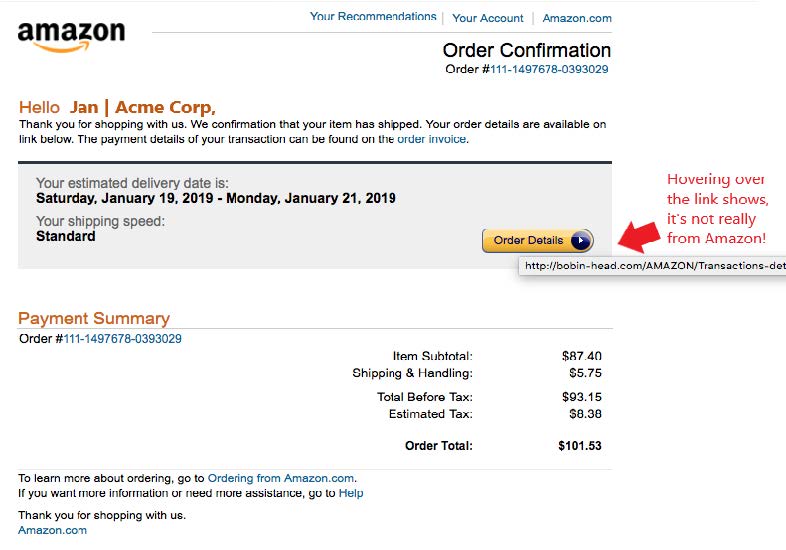
While the dark web has legitimate privacy uses, it’s also where cybercriminals trade in stolen credentials, Social Security numbers, financial records, and more. Once your data appears here, it can be copied, distributed, and resold endlessly, making full removal virtually impossible.
Can Data Be Removed From the Dark Web?
The unfortunate truth is: once data reaches the dark web, full removal is unlikely. Its decentralized nature and lack of legal oversight mean there’s no governing body to request takedowns from.
However, Black Diamond Solutions offers tools and monitoring solutions that can help limit further damage, identify risks early, and put safeguards in place to protect you or your business from identity theft and fraud.
Understanding the Challenges of Data Removal
Dark web forums and marketplaces are not regulated. Many are hosted on overseas servers and protected by layers of anonymity. Once your personal or business information is listed, it’s often copied multiple times and shared across various sources. That’s what makes traditional “takedown” requests ineffective.
Proactive Measures for Protection
While you may not be able to erase your data from the dark web, you can take powerful steps to protect yourself and minimize risk. Here’s how:
Identity & Credit Monitoring
Use monitoring services that scan for your email, passwords, or financial data on the dark web — and alert you if it shows up. Our Chicago cybersecurity team can help you get started.
Strong Password Hygiene
Create strong, unique passwords for each account and turn on two-factor authentication. A breach on one site shouldn’t mean access to everything you use.
Use of Privacy Tools
Remove your data from people-search sites and data brokers using services like Optery, Privacy Bee, or manual opt-outs. We can help identify where your data is most at risk.
How Can I Enhance My Digital Security?
Removing Personal Information from Data Brokers
Data brokers scrape public records and online activity to create profiles that can be exploited. Black Diamond Solutions can help Chicago residents and small businesses opt out and reduce exposure.
Implementing Robust Security Practices
Enhance your cybersecurity posture by doing the following:
- Use complex passwords and store them securely
- Enable two-factor authentication (2FA)
- Keep all devices and software updated
- Use a VPN to keep your browsing private
- Avoid clicking on suspicious emails and attachments
What to Do If Your Information Is Found on the Dark Web
Immediate Actions
- Change all affected passwords immediately
- Enable MFA on all sensitive accounts
- Notify your bank or credit card provider of any unusual activity
Long-Term Strategies
- Use a password manager to generate and store secure credentials
- Monitor your credit and online accounts regularly
- Work with a trusted Chicago-based value-added reseller like Black Diamond Solutions to integrate long-term cybersecurity monitoring into your broader IT strategy
Work with Chicago’s Cybersecurity Experts
Your digital security is too important to leave to chance. At Black Diamond Solutions, we offer professional dark web monitoring, data breach recovery, and cybersecurity services in Chicago for both businesses and individuals.
If you’re worried that your information is already on the dark web — or simply want to be proactive — contact us today. Our cybersecurity experts will help you assess your exposure and build a plan to keep your data secure.